26 minutes
CybersecUpdate 1 : Notes and Insights
Salam Alikum,
I finished the Tryhackme’s PreSecurity Pathway and all the notes will be available down below. A hurdle that comes while learning , for me is making notes while learning basic things, that I’m familiar with already. The note taking process is important and can’t be skipped because of the forgetting curve as we e tend to forget things after a certain period of time. Even if it’s about basic concepts that I know already, documenting what I study is important.
I also found something very powerful that helps me stay focus for hours on end. I found this https://youtu.be/cuJ9L5aBvio?si=Y3EknnUeziAfFzWz particular audio very helpful while I’m studying or doing any task that requires focus. this is a 432 Hz sound . What happens I believe is that without the sound there are many distracting factors around, people talking, walking, general sounds of the surroundings ( even when I’m in the library ), but with this audio running in the background, all those sounds are filtered out and one sound is present, this 432 Hz Frequency. This significantly increases my focus as now instead of 10 things stealing my focus there’s only one constant monotonic sound.
About the notes, I’ve made notes for my utility and want to share here for the benefit of anyone reading this blog. I thought of changing the plan and posting the notes with titles of 1a , 1b , 1c, 1d … 1z for each cybersecurity update post. But found that it’ll be more difficult to navigate then to put them all in one post for each week. so I’ll do my best to structure the notes under headings and subheadings.
I’m also making notes for Advent of Cyber 2024, which will be released as one Separate Mega Blogpost on 1st January when the Event ends. it’ll contain insights about each challenge and the technologies involved.
Notes
Networking
Networking : A set of nodes connected by connection links.
Packet
- The state of Data( also known as PDU ( Protocol Data Unit) ) when it’s in the Network layer is called a Packet
- Consists of
-
Header
- Trailer
- body
Difference between UDP and TCP Packet Headers
| Field | TCP Header | UDP Header |
|---|---|---|
| Protocol | Always 6 (indicates TCP protocol) |
Always 17 (indicates UDP protocol) |
| Source Port | Present | Present |
| Destination Port | Present | Present |
| Length | Not present (length is implied by the total length) | Present (specifies the length of the UDP header + data) |
| Sequence Number | Present (used for ordering and ensuring reliable delivery) | Not present (UDP is connectionless and does not require ordering) |
| Acknowledgment Number | Present (used for acknowledgment in reliable communication) | Not present (UDP does not guarantee acknowledgment) |
| Data Offset | Present (specifies the length of the TCP header) | Not present (fixed 8-byte UDP header) |
| Flags | Present (e.g., SYN, ACK, FIN for session management) | Not present (UDP is connectionless and has no flags) |
| Window Size | Present (for flow control) | Not present (UDP has no flow control) |
| Checksum | Present (for error checking header and data) | Present (for error checking header and data) |
| Urgent Pointer | Present (indicates urgent data) | Not present (UDP does not support urgent data) |
| Options | Optional (for additional control information) | Not present (fixed-size UDP header) |
-
Characteristics of a Computer Network :
- fault tolerant
- Scalable
- Quality of service
- Security
-
Data Communication
- Transfer of data between nodes by a transmission medium
-
Protocols are the rules that govern methods of communication between two nodes
-
Protocols
-
Rules that govern communication between nodes in a network
Example ( Human Communication Protocol )
- Same language
- Audible tone
- Sender / reciever etc
- total 65535 protocols ( each for UDP and TCP )
- Protocols define ( Elements of Protocol )
- Message size
- Messages should be sized so the transmission medium can handle them.
- if the message is bigger then the average packets the receiver can handle at a time, then the sender sends in smaller packets , each Part of the big message is sent in numbering order or sequentially, after all the small packets that make up the message are sent to the receiver ,the receiver counts them to find if something’s missing. 1
- Message timing
- Flow control
- flow should be balanced, else if the sender is fast and receiver is slow, the receiver won’t receive the data when intended , a flow control mechanism controls this.
- The receiver sends the sender the amount of packets it can handle at a time and then the sender sends the packets in that speed
- Response Timeout
- The receiver has to Acknowledge that it got the data from the sender, if it doesn’t send acknowledgement after a set period of time , after the expiry of that time, the sender sends it again , so to ensure the data is received by the receiver
- Flow control
- Message Encoding
- Message Source -> Encoder -> Transmitter -> Transmission medium -> Receiver -> Decoder -> Destination medium
- encapsulation and formatting
- Encapsulation means , when data moves from sender to receiver , it goes through the tcp/ip or OSI models , every layer in these models adds its own information to the original data, that we call a header, these headers encapsulate one by one the message.
- Message formatting means the layout and structure of the data being sent, the sender and user have to agree on a common format to be able to receive and send information and be able to understand it.
- Three Components:
- Header ( Metadata) -> Source/ Destination address, protocol information, date etc
- Payload -> The actual data
- Footer ( Trailer) -> contains FCS ( frame check sequences), Checksum, Error checking information
- Three Types of Formatting:
- fixed -> Predetermined Structure with fixed fields and lengths
- Variable -> Flexible and adapts to the message sizes and types
- Hybrid -> combination of fixed and variable
- Three Components:
- Delivery options
- unicast -> one sender , one receiver
- multicast -> one sender , Multiple receiver ( not all )
- Broadcast -> one sender , All participants of the network
- Message size
- Types
- Main protocols are from 0 to 1024
- FTP = 21, 20
- SSH = 22
- Telnet = 23
- not very secure like SSH
- Peer to Peer networks, is decentralized , no one is an administrator.
- Client Server Networks, a server , connects all the clients, or sends information to clients
- request / response model
- master / slave
-
Components of a Network
-
Nodes
- nodes are anything in the network that can receive / send or both, information to another node in the network
- End Nodes:
- These are the nodes where the Data either Originates or Terminates
- accepts the communication at the end, or Initiates the communication from the start
- Intermediate Nodes:
- These are the nodes which help Relay information to another intermediate node or an end node ( that is not an origin node)
- switches, bridges, WAC ( Wireless Access points ), cell tower etc.
Medium
- Wired Medium
- Ethernet
- Straight through ( for internet ) -> connect Different kinds of devices
- Switch -> Router
- VoIP -> Router
- Crossover ( two routers ) -> Connect same kinds of devices
- Router -> Router
- Movement by Electrical signals
- Straight through ( for internet ) -> connect Different kinds of devices
- Fiber Optics
- Movement by light waves
- Coaxial Cable
- Audio or Video communication -> TV Cable,
- Movement by Electrical Signals
- USB Cable
- Computer to a smartphone etc
- Ethernet
- Wireless Medium
- Infrared -> Short range ( tv control)
- Radio -> Bluetooth , wi-fi
- Microwaves -> Cellular Systems -> long distance
- Settalite -> GPS, etc
Services
- can be anything
em
Network Topology
- Arrangements of nodes in a network , layout such that each node communicates with the the other node in the network
- Physical Topology
- Physical placement or layout of nodes
- Logical Topology
- Data flow to and from nodes in a network
- Types
- Bus
- Common transmission medium, means , all the nodes are connected to one single ‘bus’ medium , and data first node if it wants to move to 10th node, would move by all the intermediary nodes / All nodes receive signals simultaneously , bidirectional
- no fault tolerance ( if the main medium breaks, then rerouting can’t be done)
- no security
- Common transmission medium, means , all the nodes are connected to one single ‘bus’ medium , and data first node if it wants to move to 10th node, would move by all the intermediary nodes / All nodes receive signals simultaneously , bidirectional
- Ring
- Bus topology but in a ring like formation
- unidirecitonal and each node is connected to two neighboring nodes, left and right, and at a time, the information can move at one side, moving through other nodes to find it’s destination node
- Token is used to send data, whichever node has the token, has to send data, eventually the token is passed /circulated to other nodes by time, and that’s how we make sure every node has the chance to send data.
- no fault tolerance / unidirectional
- no security
- No. of Ports : 2N,, Cables : N
- Star
- every node is connected to a central node ( hub or [[switch]] ) , this hub connects all the nodes, everytime a node sends data to another node, it moves through the hub first.
- may bottleneck due to overloading
- two star topologies can be connected with the help of a [[repeater]]
- **No. of Ports 2N ** , Cables : N
- every node is connected to a central node ( hub or [[switch]] ) , this hub connects all the nodes, everytime a node sends data to another node, it moves through the hub first.
- Mesh
- one node gives off links to all the other nodes in the network, directly,
- fault tolerance, reliable
- scalable
- expensive / broadcasting can give issues
- **No. of Ports : N(n-1) ** , Cables : N( N-1) / 2
- one node gives off links to all the other nodes in the network, directly,
- Hybrid
- one or more different topologies in one network .
- Bus
- Ports
- the movement to and fro nodes, is done by ports, depending on the topology , each node can differ in the number of ports it has, for example in a ring topology with 2 nodes, there are 2 cables, 2 nodes, and each node has 2 ports, so total ports become , Nodes X No. Of Ports Per Node = 4
IP Address
- Address of a node in a network is IP Address ( Internet Protocol Address)
- Types
- IPv4:
- creates 32 bit IP Addresses
- changes based on location
- its’ logical address because can be changed based on location
- assigned manually or dynamically
- represented in decimal and 4 octets ( 4 parts x.x.x.x ) x can be a value between 0 and 255
- these 4 parts are further divided into two parts,
- the first three octets, show which network the device is on ( Network ID)
- the last octet is the host ID which identifies the specific device on that network
- IPv6
- 128 bit IP Addresses
- created to fulfill limitations in the availability of IPv4 to only 4 billion devices, even with NAT involved, it was a need to create IPv6
- 340 undecillion combinations
- contains alphabets, numerals, quartets, symbols separated by colons instead of a dot.
- Dual stacking means, ,both protocols IPv4 and IPv6 running at the same time
- IPv6 tunnels allow to devices to communicate even with different IPv versions
- more secure then IPv4 ( bounded to become the norm)
- IPv4:
- Can be
- Static -> IP address is permanent ( mostly for servers )
- Dynamic -> changes every time connected to the internet
- if DHCP ( Dynamic Host Configuration protocol ) is present , it’ll dynamically assign IP addresses to the devices, every time they’re connected to the internet,
- public and private IP
- public IP is usually not changing and private IP can be dynamic , public IP’s need constant security measures as they’re available, on the other side private IP’s could only be attacked if the attacker is in the same network that’s why they’re also called local IP’s , start with 10.0.0.0 and 172.67.0.0 ranges.
- Network Address Translation
- Enables to represent multiple devices with a single IP Address for IPv4
Subnetting
- dividing the networks into multiple IP’s is called subnetting
ARP
- Two parts
- ARP request
- ARP reply
- Stored in ARP cache , the main function of the ARP request is to send ARP packet to each device in the network to find out what MAC Address is associated to an IP Address
DHCP
- Dynamic Host Configuration Protocol
- Sets IP addresses to devices in the network automatically ( first come first serve basis )
- Configured in Router , Or Dedicated server for large organizations and sometimes Layer3 switches
- when a device connects to a network and it hasn’t been assigned an IP manually beforehand. IT sends a
- DHCP Discover Request
- if there is a DHCP server in the network it replies with a
- DHCP Offer ( IP Address )
- then the device sends a reply saying it wants the IP address
- DHCP Request
- now the DHCP server sends Acknowledgement that it’s been completed and sends
- DHCP ACK
MAC Address
- Name of a node is the MAC Address, the location ( IP Address) may change but the MAC Address doesn’t change because it’s inherent to the device/ node
- Physical address / hardware address ( Not Logical )
- cannot be changed, assigned by manufacturer
- Represented in Hexadecimal -> 48 bits and separators can be decided by the manufacturers
- can be 08-d2- 131-11 or 08.d2.131.11
- 12 digits, first 6 give the Manufacturer and the other 6 give the Network Interface Card ID
Port Addressing
- Port Addressing
- Reaching a network -> IP address
- Reaching the host -> MAC address
- Reaching the process -> Port Address
- In a system / pc / phone etc , multiple processes are running simultaneously, each process has a port address, basically when it asks for information from other nodes, it expects the information to reach it’s host address, not just reach the host and the story ends, the process that asked for the information from other node, should be given the information and that’s made sure by the port address of the process/ service that’s running
- it’s called a Communication endpoint
- fixed or dynamic
- can be between 0 to 65535
Switch
- Switches determine the best approach to move the data to desired location
- one to one connection
- Types
- Circuit Switching
- path between sender and receiver
- first connection is made, then data is transferred
- Message Switching
- Store and forward mechanism
- sender sends big data , it’s broken down into small pieces, and then the intermediary nodes get the small pieces and then it connects all the packets and then sends complete data to the destination node
- Packet Switching
- Internet
- message is broken down into small packets , unlike message switching , the packets can be sent independantly, so how are they organized? they’ll have the sender and receiver IP addresses, MAC and host etc, also a sequence number to rearrange the packets on the receiver’s end.
- when the packet is sent to the receiver, if the receiver doesn’t send the acknowledgement back to the sender in a set period of time, response time. it sends again.
- Two types
- DataGram Packet switching
- Connectionless ( different routes by datagrams)
- Path is not fixed for each packet which in this case is called a datagram
- each data gram has a destination address
- similarly each datagram has a sequence number so the original message can be reconstructed back.
- Virtual Circuit Switching
- Connection oriented ( fixed routes)
- A virtual circuit identifier is used to make fixed connection path.
- Call request and call Accept packets are sent to make a logical connection, that’s fixed
- DataGram Packet switching
- Circuit Switching
Network Layering
Protocols
Rules that govern communication between nodes in a network
Example ( Human Communication Protocol )
- Same language
- Audible tone
- Sender / reciever etc
- total 65535 protocols
- Protocols define ( Elements of Protocol )
- Message size
- Messages should be sized so the transmission medium can handle them.
- if the message is bigger then the average packets the receiver can handle at a time, then the sender sends in smaller packets , each Part of the big message is sent in numbering order or sequentially, after all the small packets that make up the message are sent to the receiver ,the receiver counts them to find if something’s missing. 1
- Message timing
- Flow control
- flow should be balanced, else if the sender is fast and receiver is slow, the receiver won’t receive the data when intended , a flow control mechanism controls this.
- The receiver sends the sender the amount of packets it can handle at a time and then the sender sends the packets in that speed
- Response Timeout
- The receiver has to Acknowledge that it got the data from the sender, if it doesn’t send acknowledgement after a set period of time , after the expiry of that time, the sender sends it again , so to ensure the data is received by the receiver
- Flow control
- Message Encoding
- Message Source -> Encoder -> Transmitter -> Transmission medium -> Receiver -> Decoder -> Destination medium
- encapsulation and formatting
- Encapsulation means , when data moves from sender to receiver , it goes through the tcp/ip or OSI models , every layer in these models adds its own information to the original data, that we call a header, these headers encapsulate one by one the message.
- Message formatting means the layout and structure of the data being sent, the sender and user have to agree on a common format to be able to receive and send information and be able to understand it.
- Three Components:
- Header ( Metadata) -> Source/ Destination address, protocol information, date etc
- Payload -> The actual data
- Footer ( Trailer) -> contains FCS ( frame check sequences), Checksum, Error checking information
- Three Types of Formatting:
- fixed -> Predetermined Structure with fixed fields and lengths
- Variable -> Flexible and adapts to the message sizes and types
- Hybrid -> combination of fixed and variable
- Three Components:
- Delivery options
- unicast -> one sender , one receiver
- multicast -> one sender , Multiple receiver ( not all )
- Broadcast -> one sender , All participants of the network
- Message size
- Types
- Main protocols are from 0 to 1024
- FTP = 21, 20
- SSH = 22
- Telnet = 23
- not very secure like SSH
The OSI Reference Model
-
Open Systems Interconnection Model
-
allows communication between two completely different systems, with ease and smoothly.
-
Encapsulation Decapsulation
- PDU ( protocol Data Unit) formatted data name in each layer.
- Encapsulation occurs when the data is going from Application layer to physical layer
- Decapsulation occurs when data moves from Physical layer to Application layer
-
Please don’t throw sausage pizza away
- Application Layer
- File transfer and access management
- Mail services
- Directory Services
- Presentation Layer
- Syntax and semantics of the message being sent
- what does the first few bits represent, whats the meaning of other sections, etc,
- Translation
- Data from one computer to another, The data is formed into a common format so it’s acceptable by the receiver
- Encryption
- Securing the data by encryption, unreadable message , decryption on the receiver’s end
- Compression
- reducing the number of bits in the information to reduce bandwidth loss
- Syntax and semantics of the message being sent
- Session Layer
-
establishes, maintains and syncs interaction between devices
- contains “Checkpoints” in specific parts of the established sessions to see whether some data is lost or not ,if yes, it resends only the newest packet ( data ) to save bandwidth
- If a connection is interrupted mid session, the connection is resumed from the last checkpoint ( efficient and Bandwidth saver)
- contains “Checkpoints” in specific parts of the established sessions to see whether some data is lost or not ,if yes, it resends only the newest packet ( data ) to save bandwidth
-
Dialog Control
- communication between two computers by any of the
-
Data flow
- Simplex
- Unidirectional
- one node transfers , the other receives ( Keyboard, monitor etc)
- Half Duplex
- Both directions ( not at the same time)
- one sends, the other receives, not at the same time ( walkie talkie )
- Duplex
- Both directions ( same time )
- one sends, the other receives , can do at the same time ( Telephones)
- Simplex
-
Synchronization
- adds sync points or checkpoints, if a large file is being sent between two computers, there are checkpoints that ensure after a set packet transfer that the packets are sent successfully and if a crash occurs, only the one that’s not sent is sent again ( packet )
-
- Transport Layer
- PDU : data becomes Segment
- Adds Src And Dest. Port Numbers
- Could be Transmission Control protocol
- Could be User Datagram Protocol
- Network Layer
- PDU : Segment Becomes Packet
- Adds Src. Des. IP addresses
- Protocols that Determine the route taken by the Packets:
-
Open Shortest Path First Protocol
- Routing protocol
- Called Link-state routing because the routers share the state of their links with other routers.
- Hello packets are sent by the router to neighboring routers , every 10 seconds for ethernet, to find whether the neighboring routers are reachable ( alive or dead), once that’s done, LSAs are sent.
- Application Layer
-
Each router sends LSAs ( Link state Advertisements ) to All other routers in the network (OSPF area ) to map out the whole network ( unlike distance vector it makes it’s own map of the network ) ,
- LSA contains detailed information about the router’s LINKS ( the links of the routers that sends the LSA to other routers)
- Makes sure that all the routers have same link-State table ( mapping )
- Can be LSA1 ( router ) , LSA2 ( Network ) , LSA3 ( Summary )
| Type of Update | Triggered LSAs | Periodic LSAs |
|---|---|---|
| When Sent | Only during a topology change. | At regular intervals (default: 30 mins). |
| Purpose | Immediate convergence after changes. | Maintain consistency and prevent stale data. |
| Frequency | As needed. | Regularly, regardless of network changes. |
- Dijkstra algorithm is used to calculate the shortest path , ( the network has ben mapped previously)
| Aspect | RIP | OSPF |
|---|---|---|
| Protocol Type | Distance-vector | Link-state |
| Metric | Hop count | Cost (bandwidth, delay, etc.) |
| Updates | Periodic broadcasts (every 30 secs) | Triggered (changes only) |
| Scalability | Limited (15 hop max) | Suitable for large networks (Divides the Network into Areas ( Area 0 is the Backbone)) |
| Convergence | Slower | Faster |
| Complexity | Simple configuration | More complex setup |
-
Routing Information Protocol
- Routing protocol
- Distance Vector routing because it uses
- Distance
- Number of hops ( router ) the packet needs to reach the destination networks’ router.
- Vector
- Direction or next hop
- Distance
- to follow the best path for the packet to travel
- Each router shares it’s ROUTING TABLE with only it’s neighbors , each router knows only what it’s neighbor tells it. Periodically.
- Bellman ford algorithm ( unlike Dijkstra algorithm in OSPF )
-
Data link Layer - PDU: Segment Becomes Frame - Adds Physical Addresses ( Mac Addreses ) Src , Dest. - takes data from Network layer ( with IP of receiving endpoint ) and ADDS MAC address of the receiving endpoint ( NIC has MAC Address ) - The only time a Header and a trailer is added to the packet to make it a frame
- Physical Layer
- Frame Becomes Bits
- Physical Layer
-
The intermediary Nodes leading to the destination node, cannot touch the data other then Network, Data link and Physical Layer, because that’s private information.
PDUs at Different OSI Layers:
- PDU stands for Protocol Data Unit, It’s basically the formatted unit of data at EACH layer , because in each layer new set of information is added to the data, so the data changes.
| OSI Layer | PDU Name | Description |
|---|---|---|
| Application | Data | Raw application-level information (e.g., HTTP requests). |
| Presentation | Data | No change; still considered “data” at this layer. |
| Session | Data | Maintains session-related information (still “data”). |
| Transport | Segment (TCP) Datagram (UDP) | Includes port numbers and ensures end-to-end communication. |
| Network | Packet | Contains IP addresses and routes data between networks. |
| Data Link | Frame | Contains MAC addresses and error-checking information for local delivery. |
| Physical | Bits | Data is converted into electrical signals or light pulses for transmission. |
The TCP-IP Model
- Condensed version of the OSI Model with only 4 layers
- Four layers:
- Application
- Transport
- Internet
- Network interface
Three-Way handshake
- Preamble to a secure connection between two devices
- SYN ( sending a synchronization request )
- SYN/ACK ( acknowledging the synchronization request )
- ACK ( acknowledging the connection )
- FIN ( closing the Connection cleanly )
- RST ( abruptly closing the connection )
- DATA ( The actual Data is sent to and fro the Client and server )
Port Forwarding
-
Port Mapping
-
It allows private networks to connect to the internet and ultimately be accessible to other machines in the internet to connect. or request connection
-
Technique that allows External network devices to communicate with Internal network ( private ) devices.
-
Ports
-
ports are the logical endpoints that allow services and programs to communicate over the internet
-
16 bit number ( port number )
-
range 0 to 65535
-
This allows multiple services ( with different ports ) to run on a single IP address, making it possible for multiple services to run on a single computer.
-
Network Address Translation NAT
-
It hides the internal IP of the machine and uses a public IP , as the private IP’s ( ipv4 ) aren’t usable in the internet
Firewalls
- Firewalls is a network control device that monitors the incoming and outgoing traffic in a network
- can be stateless and stateful ( primary types )
Comparison: Stateless vs. Stateful Firewalls
| Feature | Stateless Firewall | Stateful Firewall |
|---|---|---|
| Connection Awareness | Does not track connection states; evaluates packets individually. | Tracks and monitors the state of active connections. |
| Operation Layer | Operates at Layer 3 (Network Layer). | Operates at Layer 4 (Transport Layer) and higher. |
| Security Level | Basic filtering; less secure and vulnerable to spoofing attacks. | Advanced filtering with connection context; more secure. |
| Processing Speed | Faster and less resource-intensive. | Slower due to tracking and higher processing requirements. |
| Rule Set Complexity | Simpler rules; only focuses on headers like IP, port, and protocol. | Dynamic rules based on connection states and context. |
| Example Scenario | Block all traffic from a specific IP address or port. | Allow HTTP responses from a server after an outgoing request. |
| Use Cases | Small, simple networks or routers. | Enterprise environments or networks requiring high security. |
- Stateless firewalls are like a security guard that don’t remember what visitor came in or out, and whenever a new visitor comes, it just checks the list ( already set rules and values) to either let them in or not, like ( source / destination port), i.e if it’s asking to go to port 123 through door A then let it in otherwise no. etc etc
- works in layer 3 ( Network Layer ( IP addressing & routing )) , so just concerned with Protocol and the port number and destination and source Port IP .
- inspects individual packets
- Stateful firewalls are those security guards that remember exactly who went through the network and when. they make more calculated and informed decision but use more resources ( it understands the flow of conversation )
- it works in Layer 4 ( Transport Layer ( TCP / UDP > delivery ) ) has access to TCP UDP Headers, Syn ACK info, sequence numbers etc.
- inspects the Whole network
- They usually work in layer 3 and 4
Virtual Private Network VPN
- It is a technology that allows devices to communicate with each other from different parts of the world, privately and securely
- A VPN server is setup
- When we send a packet instead of routing to the destination it moves to the VPN server, then the VPN server routes it to the destination address.
- The IP address is of VPN not ours, so it hides our IP ( Identity on the internet )
- The data is encrypted when it leaves the systems so it’s not visible in it’s raw form to anyone but the source and destination devices.
Domain Name System DNS
- Domain name system allows users to access sites without knowing their IP or port numbers in the network,
- its like a phonebook , It translates human friendly names of Websites into IP addresses, so instead of typing the IP address of the site ,you are only required to type the DNS alternative name of the site which automatically leads you to the website’s IP and Port .
Instead of going to 8.8.8.8 you just search google.com, for sites with longer and difficult to remember IP Addresses this becomes a problem so a human friendly name “Google.com” is assigned by the DNS and translated on the go.
- DNS Servers are responsible for storing DNS records and Names
- Domain names are Hierarchical and represented in the following manner
nestedSubDomain.subdomain.SLD.TLD
- TLD: Top level Domain
- Can be ccTLD or gTLD
- ccTLD : Country Code TLD > specifies the country of the registered domain
- gTLD : .org for organizations , .com for commercial purposes , .edu for educational
- SLD: Second level Domain
- Total size of the domain shouldn’t surpass 253 characters and each domain level should not be longer then 63 characters.
- DNS Records are of 5 types
- A records : Maps the domain name to an IPv4 Address
- AAAA Records : Maps the domain name to an IPv6 Address
- CNAME : Maps the domain name to another Domain name
- MX : Maps the domain name to the servers responsible for receiving emails for the Domain name, can be multiple and priority is set by numbering them
- TXT : arbitrary text data, for preventing spoofing or Domain verification
- How it works
- First your browser checks it’s cache to see whether it accessed the desired site recently , if not then it sends request to local Recursive DNS server, it then sees into it’s own cache whether the server has the records, if not ( it’s an unpopular site ), it starts a journey to find the desired DNS record, it asks the Root DNS Servers , these are the backbone of the internet, what they do is redirect you to the correct TLD server for your request, if you asked for google.com and it wasnt’ in your own DNS records or in your local Recursive DNS server, then when the request goes to the Root DNS server, it’ll direct you to the TLD server that deals with .com domains. these are also called name servers which deal with the TLD.
- Caching : Each time a DNS record is requested, it comes with a TTL ( Time to live ) , to avoid asking for the same DNS record everytime, the record is cached , and saved locally. ( has to be done within the TTL else the record is lost and should be requested again).
- Recrusive DNS Server : queries all the DNS servers until it finds the IP for the DOMAIN you’re looking for
- browser -> local Recursive DNS server -> Root DNS Server -> TLD Server -> Authoritative Server
- here the Authoritative Server is the one which stores the actual DNS records ( A, AAAA, CNAME , MX, TXT) for the requested domain
nslookup -type=CNAME google.com //replace CNAME with A, AAAA , MX or TXT etc.
HTTP
- Hypertext transfer protocol is a set of rules of communication between servers and browser clients
- HTTPS is secure version of HTTP with encrypted and authentication of server ( not an impersonator server )
- HTTP protocol has methods and headers in it’s Requests and Responses
- REQUEST:
- !
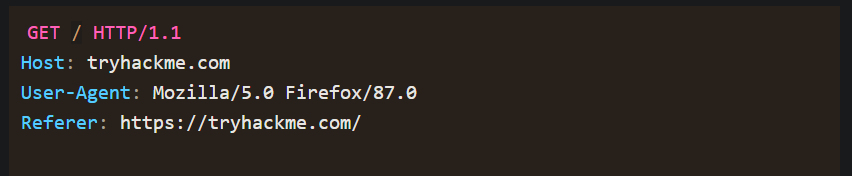
- RESPONSE :
- !
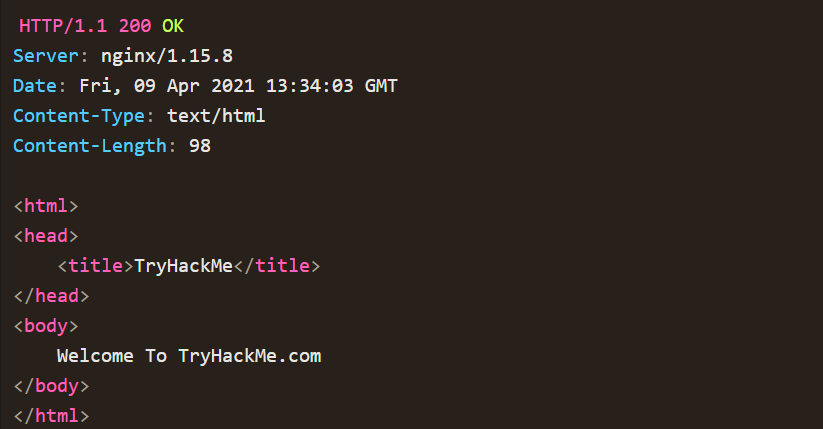
- HTTP methods
- 4 main methods
- GET Request: Request access to files from the server
- POST Request : Send data to the server and make new records
- PUT Request: Update records in the server,
- DELETE Request: delete data / records from the server.
- 4 main methods
- HTTP Status Code
- 200 - 299 Success
- 300 - 399 redirection
- 400 - 499 client errors
- 500 - 599 Server errors
- HTTP Headers
- additional information about the requests and site that is sent by the server in a response or set to the server by the client in a request.
- Cookies:
- As HTTP is a stateless protocol and doesn’t remember the past data sent or requested from the server, here’s where cookies come in, cookies are data stored in your web browser cache, what happens is when server sends an HTTP response to the browser, it also has a header named cookie-set = “Cookievalue”, this cookie value is stored in your browser , now whenever you send another request to the same server, you have a header in your request named cookie = “Cookievalue” , this helps in letting the server know where you left off last time.
- for instance if you send a request to a server and it sends a FORM back , instead of the page you requested, then you fill the form in client side and send the form, when the server sends you the page you requested originally, it’ll also send you a set-cookie header that signifies the filled fields of the form that you just filled which is telling the browser to put them in your browser and send me each time when you send another request, and the browser sends these back to the server in a cookie header, so next time instead of sending the form to the client, the server receives the cookie header and checks whether the credentials are correct and he’s logged in and sends the actual page.
load Balancers
- Load balancers sit between the server and the website and make sure that one server is not overwhelmed by the incoming requests
- when a client requests a site, the load balancer gets the request and sends it to the server based on an algorithm that it runs, that’s either round robin or weighted , to make sure that not one server is overwhelmed.
- Load balancers also do periodic checks with each server to see if they’re working properly , which are called health checks.